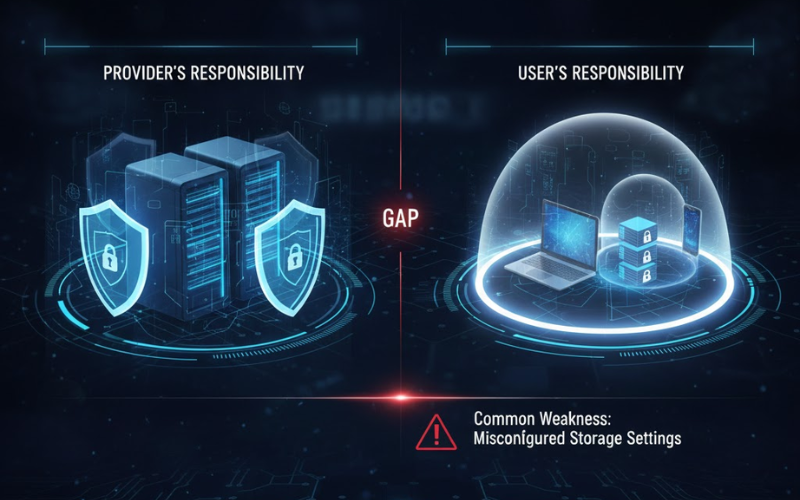
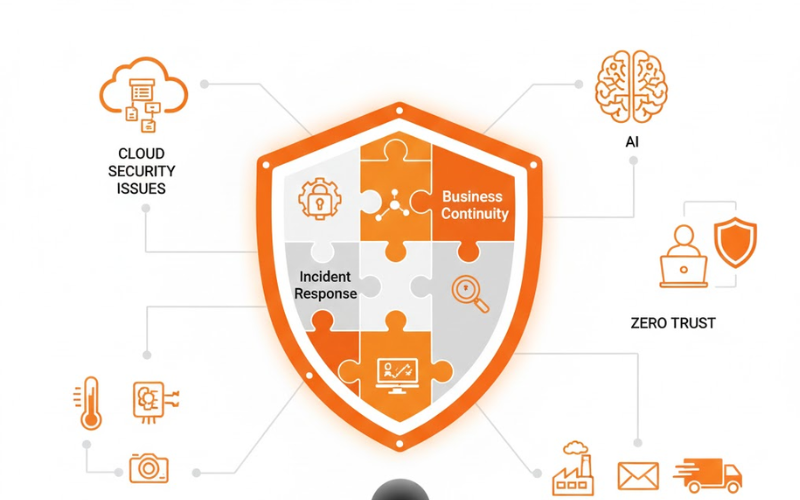
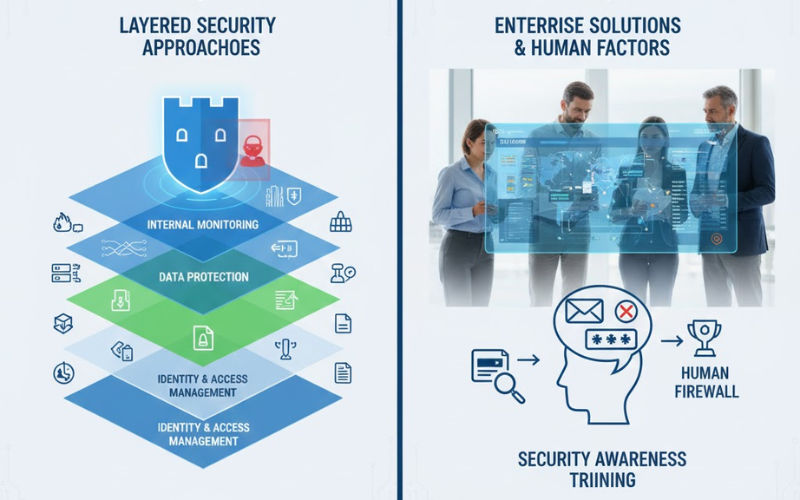
IT security solutions made clear
Imagine how fast things move now that everything runs online. Moving work to digital platforms boosts speed and opens fresh options, yet leaves companies open to clever hackers. A single break-in might drain money fast, hurt trust forever, leave private details out in the open.