Our Blogs
As leaders in the IT supply sector for over five years, we are dedicated to offering the best service that guarantees your total satisfaction.
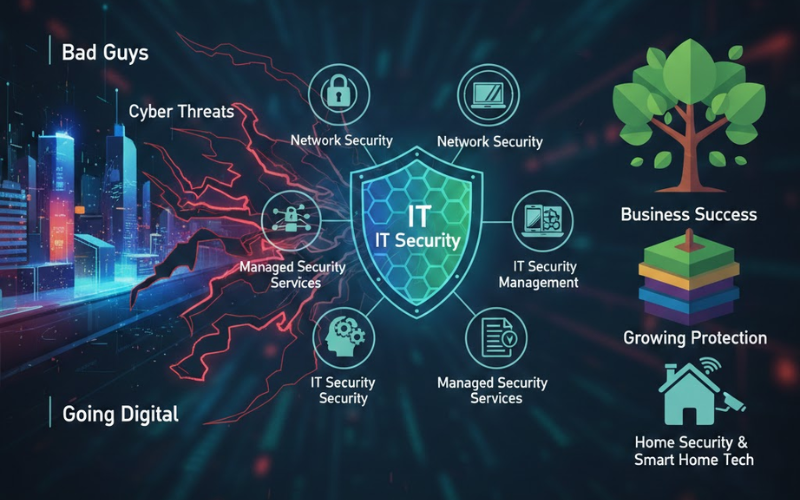
Imagine how fast things move now that everything runs online. Moving work to digital platforms boosts speed and opens fresh options, yet leaves companies open to clever hackers. A single break-in might drain money fast, hurt trust forever, leave private details out in the open.
The way we keep homes safe has changed a lot in ten years, thanks to new tech that helps families guard their houses better. Knowing what tools are out there lets people pick smart solutions - ones that stop risks without making life harder or stressful.
Pre-built computers are built for specific needs, where each part’s picked to fit what you plan to do and how fast it should run. Building one starts by choosing parts wisely - matching CPU strength, RAM size, drive speed, or GPU power while staying on budget. Experts who put them together know which pieces work well together, making sure the motherboard fits the chip, the power unit handles total demand, and fans or coolers keep things from overheating during heavy use
In today’s always-on world, companies run on tech that's never fully safe from hidden dangers. Instead of random hacks, cyberattacks now act like steady pressure aimed at soft spots in company systems - sooner or later hitting where it hurts most. A single break-in doesn't just drain money; it chips away
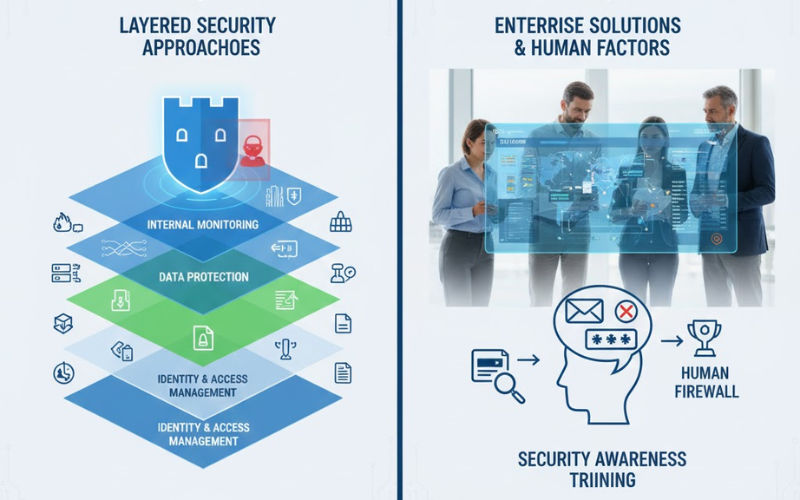
Strong checks make sure users are who they say they are before getting into systems. Instead of just passwords, rules now demand tricky combos that you swap out often - this helps a bit. Yet relying only on passwords isn't working as well these days. To boost safety, extra steps kick in using things like temporary numbers, fingerprint scans, or physical keys. When layers stack this way, it’s much harder for intruders to get through - even if they steal your password. Privileged access management keeps tight control over admin accounts with extra powers. If hackers get
The Critical Importance of IT Security Digital operations create tons of private info, so tech safety is key to keeping things running while earning user faith. A leak harms your name, brings fines, weakens loyalty - recovery often drags on forever. Firms focusing on protection early dodge costly fixes later plus chaos tied to playing catch-up. Think of security as fuel for progress instead of a roadblock slowing fresh ideas down.
The rapid shift to digital tools in nearly every field brings huge chances - but also serious risks. As companies rely more on tech systems to operate, safety isn't just for IT teams anymore; it's essential for survival. Staying aware and using strong safeguards helps defend critical data, keep clients confident, yet keeps operations running smoothly.
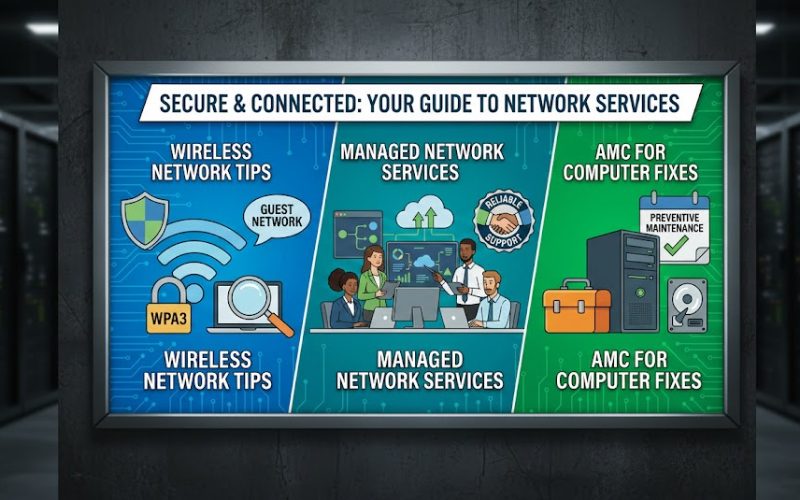
Yearly service deals keep computers running smoothly, stopping little problems before they turn into big, expensive breakdowns. Because of regular checkups, machines stay up longer, avoid crashes, while staying safer from threats. Frequent checks on equipment spot small issues before they turn serious. When you catch things like overheating or weak fans early,
Even when you try hard to stop them, cyber problems sometimes still happen. Good reaction skills reduce harm by spotting issues fast, locking things down, checking what went wrong, fixing it, then getting back online. If a company hasn’t planned how to react, they might mess up - rushing around, messing with proof, letting threats spread, or staying offline longer than needed. Incident response plans lay out steps to manage different security issues. These guides outline who does what, so
IT security outsourced help gives companies access to skilled pros who keep an eye on risks before they blow up - no need to hire a full team inside the company. More and more firms are jumping on board because staying safe online means having niche know-how, constant watch duty, plus fast reaction moves, things
Wireless networks are great because you don't need cables. That means you can move around and connect lots of stuff – laptops, phones, tablets, you name it. A good start to wireless security is scrambling your data so others can't read it, which is called encryption. WPA3 is like a super strong lock that blocks common hacking methods. Set up guest networks, too. That way, visitors
Going digital helps businesses succeed now, but it also opens doors for bad guys. IT security isn't just a tech thing anymore; it's a big business risk. Everyone in the company, even the top bosses, needs to care about it. Cyber threats are getting smarter. With rules getting tougher and breaches hurting how people see you, having good security is key for any business, big or small.
Big IT and security setups are there to back the tech and security requirements that big businesses have. These setups can grow and play well together. Many big security setups have one spot to control them and ways to tweak stuff, plus they give you the full story in reports.
The desktop computing environment has changed significantly in recent decades. Where consumers had limited choice from large manufacturers in the past, the marketplace today is extremely flexible in terms of assembled systems commissioned to particular needs and budgets. Knowing what assembled desktops bring to the Component prices vary with market conditions, availability, and technology progress. New product introductions tend to command premiums while older technology is discounted. Shortages can occasionally drive prices temporarily higher. Seasonal trends sometimes influence specific component categories. Knowledge of these market trends enables timing purchases to one's benefit.
Assembling systems includes more than just summing up component prices. Knowing what affects pricing aids in assessing quotations and making value determinations. Component prices vary with market conditions, availability, and technology progress. New product introductions tend to command premiums while older technology is discounted. Shortages can occasionally drive prices temporarily higher. Seasonal trends sometimes influence specific component categories. Knowledge of these market trends enables timing purchases to one's benefit.
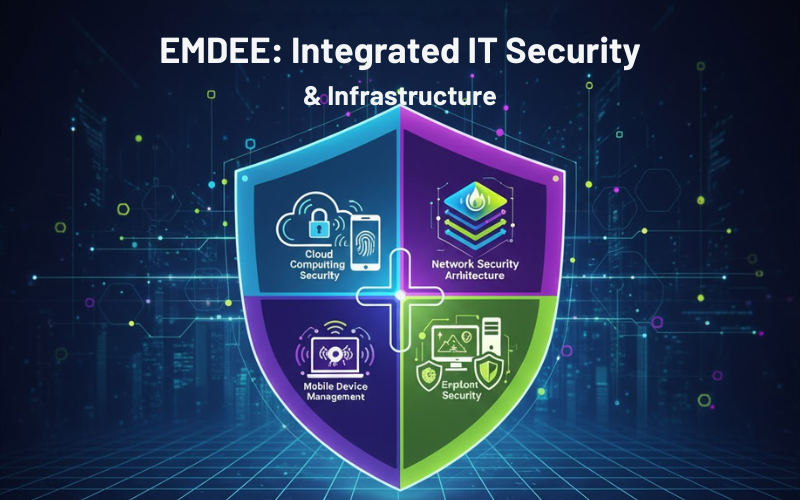
The digitalization of business processes has opened unprecedented prospects for efficiency, development, and innovation, but at the same time has left organizations vulnerable to developing cyber threats, infrastructure weaknesses, and business reliance on technology platforms. Where one
The digitalization of business processes has opened unprecedented prospects for efficiency, development, and innovation, but at the same time has left organizations vulnerable to developing cyber threats, infrastructure weaknesses, and business reliance on technology platforms. Where one
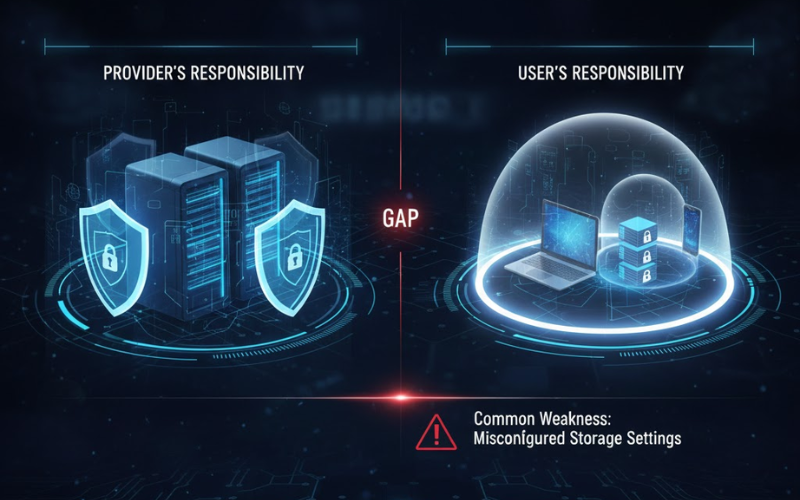
Cloud computing revolutionized IT delivery from being capital-intensive on-premises infrastructure to operationally expensed services consumed as required. Although cloud brings many benefits such as scalability, geographic distribution, and lower capital requirements, it presents special security issues necessitating alternative
The world today moves on speed, connectivity, and ease — but at the back of every click and turn is an escalating need to feel secure. From protecting a family residence, a business establishment, or sensitive company
In the rapidly evolving digital age, the decision between purchasing pre-assembled computers and assembling systems has become more and more important to both consumers and companies. Assembled desktops and laptops are a revolutionary solution to computing that gives users the
Building components for assembled desktops involves knowing current needs as well as future upgrade directions. Instead of buying the highest end components across the board, proficient builders budget strategically. They spend a lot of money on components that will have a direct impact on their main use scenario
With today's networked digital world, cybersecurity has moved from being a technical issue left to IT organizations to be a business-critical priority impacting strategic planning, risk management, and operational decision-making at the top organizational level. The rapid growth of digital transformation,
There is a dirty little secret in business that nobody is talking about. Companies are getting hacked every single day. Not only the big players that get reported on—although plenty of those as well—but ordinary businesses just trying to keep their doors open. The diner on the corner, the third-floor accounting firm, the factory on the outskirts of town. They're all considered vulnerable, and
Debris on keyboards hinders key functionality. Contamination on monitors lowers visibility and makes unfavorable impressions in professional environments. AMC laptop computer maintenance involves routine cleaning that
Connect with Us
Have an IT challenge to solve, interested in joining emdee inc., or just want to reach out? We’d love to hear from you!